This is the first article in a four-part series focused on proactively managing corporate security culture and workforce expectations as your organization prepares to prevent, detect, and respond to insider risk incidents.
I served for more than a decade in the federal space supervising and generating technical analysis on cyber, security and counterintelligence threats to inform national security strategy. I now engage with executive clients on cybersecurity risk management. My hybrid commercial and federal background uniquely positions me to bring orthogonal context to how the intersection of technology and human risk impacts business operations.
At GPSG, we believe that as cybersecurity leaders in our community we should help our clients achieve peak security performance through better understanding and managing of security risks while maintaining their pace of business operations.
Introducing an Insider Risk Program Can Be Challenging
Your organization is at risk daily for an insider incident. The cost of malicious, negligent, and credential theft incidents combined cost large, global organizations over a 12-month period close to $8.76 million, according to a recent Ponemon Institute study.
Your insider risk management plan may be met with a lack of workforce understanding of proposed policy changes, concern that it is going to set up ‘security speed bumps’ that impede workflows, or fear that it will invade their privacy.
Show Your Workforce the Need to Manage Insider Threat Risk
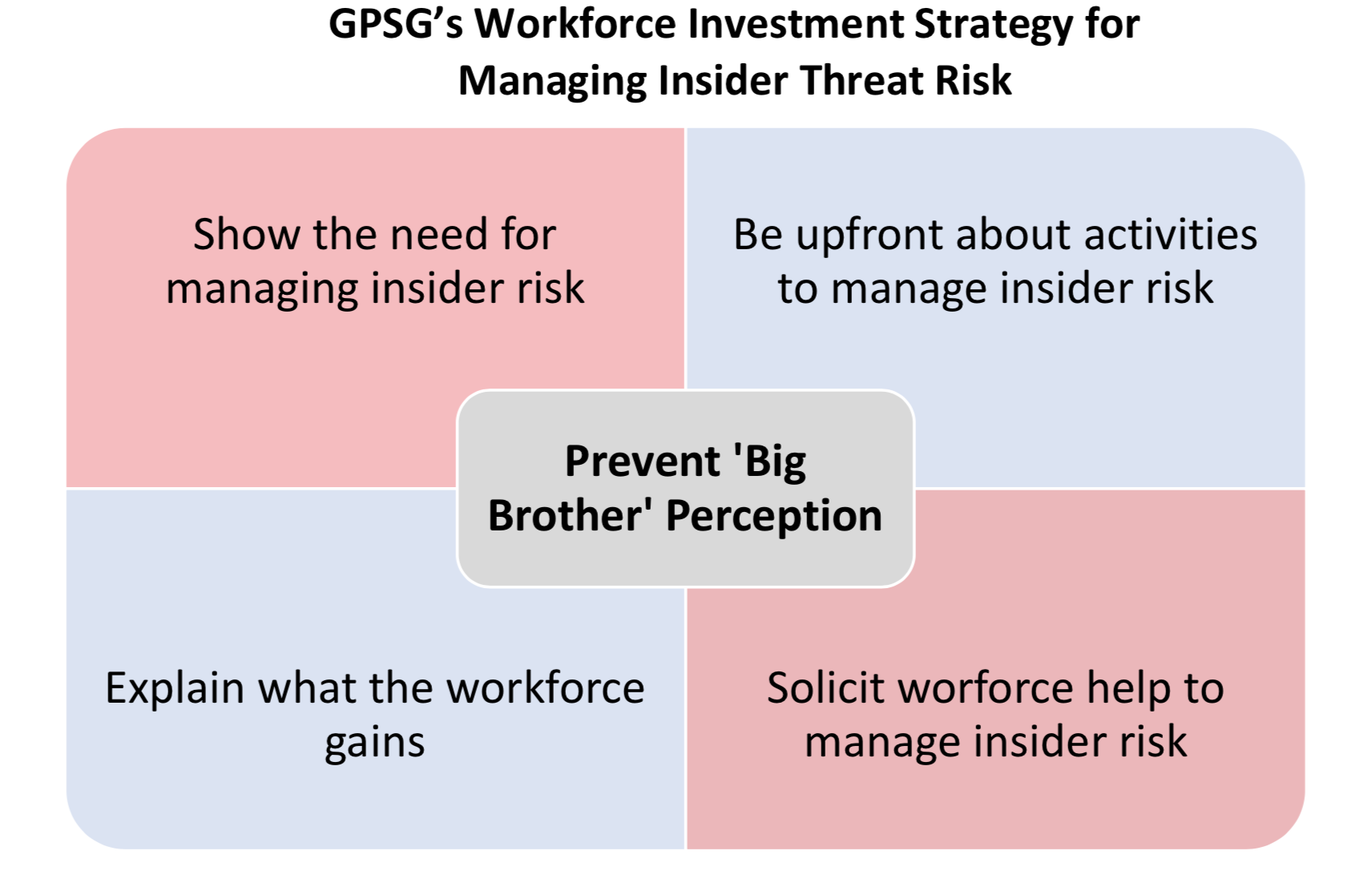
GPSG’s insider threat risk team’s four-part workforce investment strategy helps you proactively manage workforce perception and create transparency about your organization’s insider risk management goals.
How can your organization introduce the idea of insider risk management to the workforce with as much transparency and inclusivity as possible?
Assets and People Can Be Targeted by Adversaries
The first part in the strategy is to explain to your workforce why you are including insider risk management in your corporate security culture, including:
1. Increase awareness of how to protect your organization’s critical assets. Clearly communicate that the introduction of insider risk management to the already-existing security conversation is meant to ensure protection of your organization’s critical assets, including human capital. Remind them that the impacts of an insider incident may transcend stock price and shareholder value and could put the physical safety of personnel at risk. For instance, government statistics show that fatal workplace shootings are becoming more frequent and that workplace suicides are at an all-time high. Share insights and lessons learned from actual insider incidents at your organization. Above all, explain how an insider incident can negatively impact your organization’s pace of operations, corporate reputation, public trust, or employee morale.
2. Raise their awareness that they may be targeted by an outsider. First, inform them that every employee is a potential target of outsiders seeking to obtain sensitive data or harm your organization. Second, explain why they might be targeted (e.g., for financial fraud, political gain), by whom (e.g., cyber criminals, foreign intelligence services), and how (e.g., via their social media accounts, in person). For example, the case of Su Bin selling F-35 secrets to China shows how much effort and investment of time that a well-resourced outsider or adversary may be willing to exert to access your proprietary data.
3. Remind them that the security struggle is real. Share internal security stories and lessons learned with them to show that security risk is dynamic. However, security risk can be managed with careful thought, reflection, and continuous course adjustments.
4. Clarify that an insider incident can be deliberate or unintentional. An insider incident can be malicious, negligible, or merely an uninformed action conducted by well-intentioned staff. However, the potential for harm to your organization will be the same. For example, unintentional activities such as sending an email to the wrong person or misconfiguring web servers can prove costly to organizations.
Drive the Insider Risk Management Conversation
Let your workforce know in advance if you plan to conduct an insider risk assessment. Clarify who will be involved in the assessment, what their roles are, and when they will hear about any recommendations as a result of the review.
In conclusion, these are not the only steps you can take to explain to your workforce why you are including insider risk management in your corporate security culture. They help drive the conversation for your program and answer initial workforce questions about why your organization feels compelled to manage insider threat risk.
Here is the second installment in this four part series, which covers how to proactively manage and be upfront with your workforce about what your organization is doing to manage insider risk.
Contact GPSG today for a free insider threat risk management consultation at cyberteam@gpsg.co

