The challenge of identifying and communicating the most relevant cyber metrics for the board comes up frequently with our executive clients. This article provides our most recent insights and examples on cyber metrics that can help CIOs, CISOs, and other security leaders drive impactful cyber discussions with their board.
It can be challenging to communicate complex cyber issues and justify security investment to your board. However, cyber is quickly becoming a critical pulse point for resilient financial, reputational, and operational performance of most organizations today.
Cyber is a key component to the risk management of any organization, regardless of sector. With this in mind, our team explored the latest trends and insights on actionable cyber performance metrics to share with our executive clients.
For us that meant going beyond an Internet search or suggesting the quantity of phishing attacks thwarted last quarter. Rather, our goal was to highlight the qualitative aspects of actionable cyber information for a board.
Cyber Metrics Are Dynamic
We spoke to IT security leaders from the private and federal sectors, including global CISOs, CTOs, and other security executives and managers on the most impactful cyber metrics that they have seen with boards. Examples and opinions varied widely on what types of information are most useful for board room agendas today.
This reminded us that similar to our cyber adversaries’ tactics consistently changing, the cyber metrics shared with boards must also evolve to ensure relevant cyber value discussions. The cyber threat and defense landscape is in constant flux and the cyber business area’s maturity will likely differ for each organization, preventing a checklist of applicable cyber metrics.
Rather, three strategic areas came up repeatedly in our discussions as being the most critical for discussion with the board. These include cyber defense posture, cyber investment to date, and how cyber supports enterprise goals.
Communicate Your Current vs. Desired Cyber Risk Posture
Explain the current level of cybersecurity risk of critical systems to the board, along with the current budget, and what the estimated costs would be to decrease the accepted level of risk. For example, this could be illustrated with a bar chart showing your worst-case, current, and desired cyber risk postures.
Provide meaningful examples, along with cost estimates, for cyber, technology initiatives, or resources that would move your organization closer to a more desired cyber risk posture.
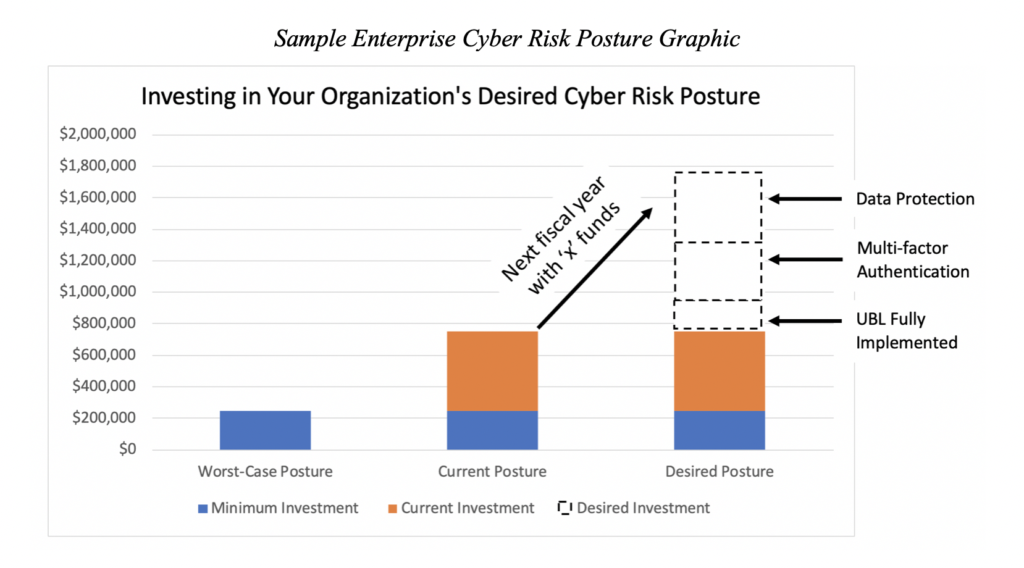
Further, if the depicted cyber resources or initiatives address any of your top cyber risks, be sure to explicitly state that with your board. Include the potential financial impacts of such risks to your company and how you came to this determination.
Here are some questions from the IT and security leaders that we spoke to that may be useful when you are preparing to address your board on your organization’s current vs. desired cybersecurity posture:
- What, if any, changes in cybersecurity posture have been made since the last time the board met on cybersecurity? Why where those changes made? What have the results been?
- What risks to critical assets are you trying to manage? From whom? Why? Does the board agree?
- What are you doing about insider threat risk?
- What is a CISO and how is that different from the CIO? How do the CISO and CIO work together on cyber risk? Does the CIO agree with the CISO’s assessment of the company’s risk and the company’s ability to respond to a cyber attack or a data breach?
- What resources does the CISO leverage to help mitigate cyber risk? For example, information campaigns, employee cybersecurity awareness training, etc.
- If you have a SOC, what does it do? How many hits vs. false positives does it spend time investigating? False positives need to be recognized as a cost waste and you should address a plan for how your organization plans to improve in this area.
- What are you doing about third-party access? Describe your grasp, or lack thereof, on third-party or contractor access to your systems and their systems that are connected to yours.
If you have a cyber expert represented on your board, you might consider addressing the following questions:
- What kind of lateral visibility (vice perimeter) do you have into things moving around your network beyond the perimeter?
- What are you doing about persistent data protection, beyond encryption at rest? For example, no matter what system the data is in or transiting, how are you protecting it?
Provide Qualitative Updates on Cyber Investments
Prepare a status update on your organization’s cyber investments or initiatives to date, including funded and unfunded projects. Emphasize that funds for cybersecurity are an investment in the long-term protection of the company’s most valuable assets vice short-term investments such as office supplies.
For example, provide the quantity of users that clicked on simulated phishing campaigns at least half of the time prior to implementing a new cybersecurity training program. Turn that into a qualitative update metric on the effectiveness of workforce training by showing a comparison to that number and the number of users that continue to click post-training, provided that amount has decreased.
Although interesting, resist focusing solely on the quantity of cyber attack attempts prevented. In our experience and from the security leaders we spoke to, the number of attacks your firewall stopped, phishing attacks thwarted, and FW and SPAM rules are not very useful to most board members. This information is not actionable and lacks context on the current state of your organization’s overall cyber posture.
Focusing on the qualitative state of your current cyber investment invites a more in-depth discussion and brings awareness to the board on what exactly more or less investment could mean to your company.
Here are some questions from the IT and security leaders that we spoke to that may be useful when you are preparing to address your board on cyber investment:
- How many cyber incidents have you had since the last board meeting? What was your response? What losses did the company take or how much did the incident cost? How will you prevent it from happening again?
- What are you currently spending on cyber protection and why? Are you spending enough to adequately protect your most critical assets?
- What is the near-term and long-term cybersecurity strategy for you organization? What are the associated costs of each?
- Is it possible to quantify the cost of not investing in appropriate cyber protection? For example, identify what could be lost and attach a dollar figure to it such as lost consumer trust which translates to a specific amount of lost revenue.
Demonstrate How Cyber Supports the Bottom Line
The IT and security leaders we spoke with shared that CISOs are oftentimes trying to determine what types of information they should be providing that will be most useful to a company’s bottom line. The answer to this question will vary by company and may change depending on the whether the organization’s cyber business area is in a development or production phase.
That said, it will be useful for you to engage with the leadership team on corporate strategy, particularly in growth and M&A issues. This will help you identify opportunities for cyber to actively support other business areas and subsequently demonstrate the value of cyber across your organization.
Ask yourself, what more could cyber be doing to help support enterprise and mission objectives? Are there compliance frameworks the company should obtain that will allow them to compete in a new market?
For example, NIST compliance would allow your company to operate in the federal space, SOC compliance would support operations in financial markets, etc. The board should be aware of what types of cyber projects could move your company into new markets or give your organization a competitive advantage.
One way to align cyber goals to help drive your board’s enterprise goals is by starting with a strategic cyber review. This type of support helps demonstrate how managing cyber risk helps ensure the integrity of your company’s systems, software, and code, which in turn protects enterprise assets.
Here are some questions from the IT and security leaders that we spoke to that may be useful when you are preparing to address your board on how cyber can help move your company forward:
- What cyber information or support can help drive your enterprise-wide initiatives forward?
- If you have fiduciary, regulatory, industry, or cybersecurity compliance requirements, are you meeting them? If not, how do you plan to meet them? What is the timeline for completion?
- As you add more cybersecurity to our organization, has it or will it make it harder for your employees to do their work? Why? What can you do about this?
Help Your Board Understand Cyber Risk
These are not the only cyber metrics that can help drive risk management discussions with your board. However, they can help the board understand how secure or insecure your organization is and how improving cyber defenses ties directly to the bottom line.
It is part of your job to identify your board’s unique cyber metrics needs. Keep in mind that different boards will ask for different things.
Get to know your board audience. Are they more technical? Are they less technical? Are they only looking to understand a few specific areas of cyber?
Arm yourself with a full understanding of your company’s value proposition to provide relevant, customized metrics for helping your board understand cyber value. This understanding and acknowledgement will allow them to make the most informed decisions about the level of risk that they choose to accept with technology or efforts to investment in.
Contact GPSG at cyberteam@gpsg.co for a free consultation on developing and aligning your cyber metrics with corporate objectives.
Disclaimer: This blog provides ever changing content, conversations, and insights on cyber threats and trending solutions that is accurate to the best of our knowledge. Although we are cybersecurity experts, we provide information which we hope is helpful, and do not endorse any specific products, tools, or solutions referenced herein. Consult with your cybersecurity team before taking any action.

